Network Scanning Methodology on a Penetration testing assessment, understand how to start enumerating a network manually and using nmap.
I will not talk about Windows or Linux, just networking stuff.
Table of Contents
Usually in certifications labs or executing a penetration test on a client we have defined in our scope a sub net with a specified range of IPs.
Before start scanning the network I usually execute some commands on my machine to verify what interface is associated with the VPN to verify my IP and verify my ARP table.
What to expect?
Networks can filter types of traffic or traffic to specific port numbers. Pay attention if you trying to get a reverse shell on a random port number, that port could be blocked. Remember ports below 1023 required root privileges to start listening.
What if the Network is blocking some types of traffic?
As I said networks can filter types of traffic like TCP/UDP/SCTP/ICMP or even IP, yes IP!
Most of the corporate networks block all traffic and only allow a tunnel between two endpoints validating src IP and dst IP, protocol type, and service/port.
UDP traffic can be blocked only for a specific host and allowed for others inside the same subnet.
Or can be blocked on all subnets or IPv6.
In these cases, we need to test the network for each host we’ve found.
Layer 1 – Detecting Hosts
Assuming we are connected to a network with a HUB we can sniff all packets on the network and identify what hosts are communicating.
Detect Hosts using Layer 2 – ARP
Ok, we have our VPN connected and we need to start enumerating the network, what can we do?
We are using Ethernet technology, ethernet has many network devices, here we are talking about layer two, what device works on layer 2?
Switches, one of the many switch functionalities is to keep track of all devices connected to it and answer all requests sent by the clients. we can create a simple sniffer with scapy to monitor all ARP traffic and detect new hosts on the same broadcast domain.
#! /usr/bin/env python3
from scapy.all import ARP, sniff
def arp_display(pkt):
if pkt[ARP].op == 1: # who-has (request)
return f"Request: {pkt[ARP].psrc} is asking about {pkt[ARP].pdst}"
if pkt[ARP].op == 2: # is-at (response)
return f"*Response: {pkt[ARP].hwsrc} has address {pkt[ARP].psrc}"
sniff(prn=arp_display, filter="arp", store=0, count=10)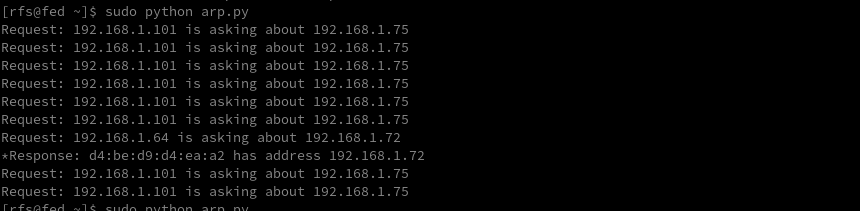
Client Side: ARP Cache
All client machines keep track of all MAC addresses from all machines on local network that all ready make a connection.
Client Side: ARP Cache
Remember a Switch maintand a table mapping all devices conneted to it! That table contains all MAC Addresses and his respective IPs connected to it.
Switch: CAM Table
Switch Side: CAM Table
L2 Attacks
- CAM Table Overflow
- VLAN Hopping
- DHCP Starvation
- ARP Poisoning
Detect Hosts using Layer 3 – IP / ICMP
We can use the ping command to send ICMP packets and verify if the host is alive but remember some hosts are configured to not respond to ICMP ECHOs, that’s why the need to pass the parameter -Pn on Nmap.
Ok at this point we detect some IPs while monitoring ARP requests, it’s time to detect what protocols at layer 3 and layer 4 are supported on the remote host. We can do that by crafting manual scripts for each protocol or using a technique IP Protocol Scan.
sudo nmap -sO 192.168.4.5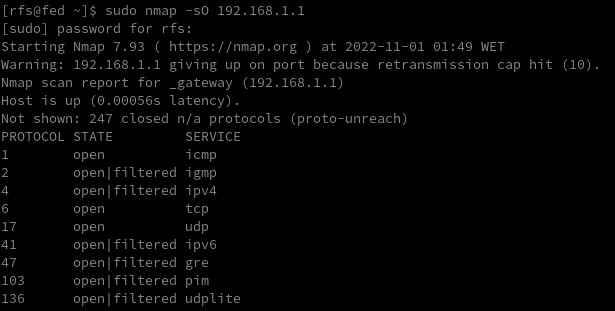
As we can see the remote host uses many protocols at both layers, we need to understand all of them not all services run on IP/TCP.
Remember to scan all 65535 ports on TCP and UDP.
L3 Attacks
- Man in The Middle
- DNS Cache Poisoning
- Reply Attacks
- IP Spoofing
- Teardrop Attacks
Layer 4 TCP/UDP: Detect Open Ports
At this point, we know what IP we need to scan and what protocols it supports its time to detect what ports are open to connections.
Nmap scan all TCP Ports
nmap -sT 192.168.4.5 -p- -PnNmap scan all UDP Ports
nmap -sU 192.168.4.5 -p- -PnWhat if we can’t connect to any port using any protocol?
Pivoting?
Traceroute using TCP
sudo traceroute -T 192.168.4.5Traceroute using UDP
sudo traceroute -U 192.168.4.5Traceroute using ICMP
sudo traceroute -I 192.168.4.5Network Scanning Methodology
Keep in Mind
You need to develop your attacking methodology here I only talk about the basics steps. Ping me on Discord to talk about other techniques. I will love it!
More notes: https://ecpptv2.popdocs.net/methodology/to-scan-a-network

Comments